The Logstash Elasticsearch plugins ( output, input and filter) support authentication and encryption over HTTP.
To use Logstash with a secured cluster, you need to configure authentication credentials for Logstash. Logstash throws an exception and the processing pipeline is halted if authentication fails.
If encryption is enabled on the cluster, you also need to enable SSL in the Logstash configuration.
In addition to configuring authentication credentials for Logstash, you need to grant authorized users permission to access the Logstash indices.
Configuring Logstash to use Basic Authentication
Logstash needs to be able to manage index templates, create indices, and write and delete documents in the indices it creates.
To set up authentication credentials for Logstash:
Create a
logstash_writerrole that has themanage_index_templatescluster privilege, and thewrite,delete, andcreate_indexprivileges for the Logstash indices. You can create roles from the Management > Roles UI in Kibana or through theroleAPI:Create a
logstash_internaluser and assign it thelogstash_writerrole. You can create users from the Management > Users UI in Kibana or through theuserAPI:POST /_xpack/security/user/logstash_internal { "password" : "changeme", "roles" : [ "logstash_writer"], "full_name" : "Internal Logstash User" }Configure Logstash to authenticate as the
logstash_internaluser you just created. You configure credentials separately for each of the Elasticsearch plugins in your Logstash.conffile. For example:input { ... user => logstash_internal password => changeme } filter { ... user => logstash_internal password => changeme } output { elasticsearch { ... user => logstash_internal password => changeme }
Granting Users Access to the Logstash Indices
To access the indices Logstash creates, users need the read and
view_index_metadata privileges:
Create a
logstash_readerrole that has theread and `view_index_metadataprivileges for the Logstash indices. You can create roles from the Management > Roles UI in Kibana or through theroleAPI:Assign your Logstash users the
logstash_readerrole. You can create and manage users from the Management > Users UI in Kibana or through theuserAPI:POST /_xpack/security/user/logstash_user { "password" : "changeme", "roles" : [ "logstash_reader"], "full_name" : "Kibana User" }
Configuring the elasticsearch Output to use PKI Authentication
The elasticsearch output supports PKI authentication. To use an X.509
client-certificate for authentication, you configure the keystore and
keystore_password options in your Logstash .conf file:
output {
elasticsearch {
...
keystore => /path/to/keystore.jks
keystore_password => realpassword
truststore => /path/to/truststore.jks 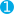 truststore_password => realpassword
}
}
truststore_password => realpassword
}
}Configuring Logstash to use TLS Encryption
If TLS encryption is enabled on the Elasticsearch cluster, you need to
configure the ssl and cacert options in your Logstash .conf file: